There is no central authority verifying any identity on the internet. You are responsible for doing the due diligence to make sure that account you’re talking to *really is* whom they claim to be.
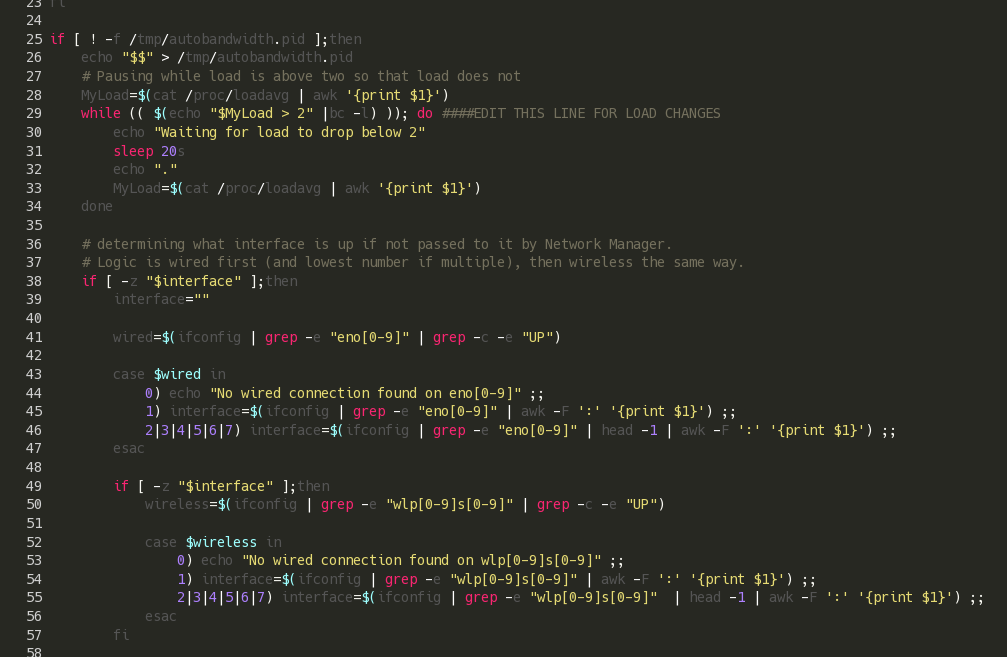
Automatically Shape Bandwidth On Linux
Automatic traffic shaping for when you change networks frequently (like with a laptop).
TELL EVERYONE: If you’re not freaking out about Net Neutrality, you’re not paying attention.
Imagine your grocery store only carried the brand of soda (or bread or soup or…) you hated. Or, worse, they’d let you get the kind you wanted – […]
Determining Who Is Home Based on DD-WRT Connections
One of the more ambitious things you can do with your phone is to have your home systems start doing things both when you leave and when you […]
Graphically See Your Home Network With jNetMap (Win/Mac/*Nix, FREE)
My home network is a little… complicated. With two routers, a switch, and multiple devices and computers attached to it, sometimes it’s useful to visually see what the […]
Run Different Programs On Connecting and Disconnecting From Networks with Both WICD and Network-Manager in Linux
So I wrote a program again. 🙂 It is (unimaginatively) named networkcontrol-wicd-networkmanager, but I affectionately call it “Bob”. It’s what I use so that I have the right […]